You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Ultra fast Nginx, SSD hosting with cPanel and Varnish Cache in Netherland
- Автор coolice
- Начална дата
coolice
Owner
I’m happy when my customers are satisfied. I will not get into details but for sure coolicehost.com has nothing in common and it is better than the average cPanel hosting that offerst you ultra hyper unlimited hosting. The prices are the same if you can get in the limits of the bandwidth and storage. We offer a more liberal usage of CPU. Can you tell how much CPU minutes you was using before coming to us? 
Последно редактирано от модератор:
coolice
Owner
Nginx in front of Apache Prestashop configuration
And something like an advertising.
PrestaShop, OpenCart (with the optimization in the product counting) Wordpress and Drupal by default* are running comfortly fast on our servers without problems with the server load but you have to do what I tell you about the settings.
PS: We fully support Google Page Speed Service – we list the true ip addresses of the users that came through the google service, most of the services offer this only for cloudflare. Never heard of an other hosting service that is doing this at our level.
And something like an advertising.
PrestaShop, OpenCart (with the optimization in the product counting) Wordpress and Drupal by default* are running comfortly fast on our servers without problems with the server load but you have to do what I tell you about the settings.
PS: We fully support Google Page Speed Service – we list the true ip addresses of the users that came through the google service, most of the services offer this only for cloudflare. Never heard of an other hosting service that is doing this at our level.
Последно редактирано от модератор:
coolice
Owner
How to Translate Apache's "RewriteRule" into Nginx's
Like I wrote in the personal message we don’t offer that for now. I’m thinking about that, but for now the first priority is to offer the greatest shared hosting configuration out there that is stable and secure. After doing this I will continue developing the other stuff.
Like I wrote in the personal message we don’t offer that for now. I’m thinking about that, but for now the first priority is to offer the greatest shared hosting configuration out there that is stable and secure. After doing this I will continue developing the other stuff.
Последно редактирано от модератор:
the.rampage.rado
Well-Known Member
coolice каза:I’m happy when my customers are satisfied. I will not get into details but for sure coolicehost.com has nothing in common and it is better than the average cPanel hosting that offers you ultra hyper unlimited hosting. The prices are the same if you can get in the limits of the bandwidth and storage. We offer a more liberal usage of CPU. Can you tell how much CPU minutes you was using before coming to us?
Not a lot, because the site was not visited by a lot of visitors, but let’s say an average of 30 minutes. Of course it will do good with bigger websites.
Последно редактирано от модератор:
N.JELQZKOV
New Member
I’ve sent a message to you, Coolice! 
Последно редактирано от модератор:
coolice
Owner
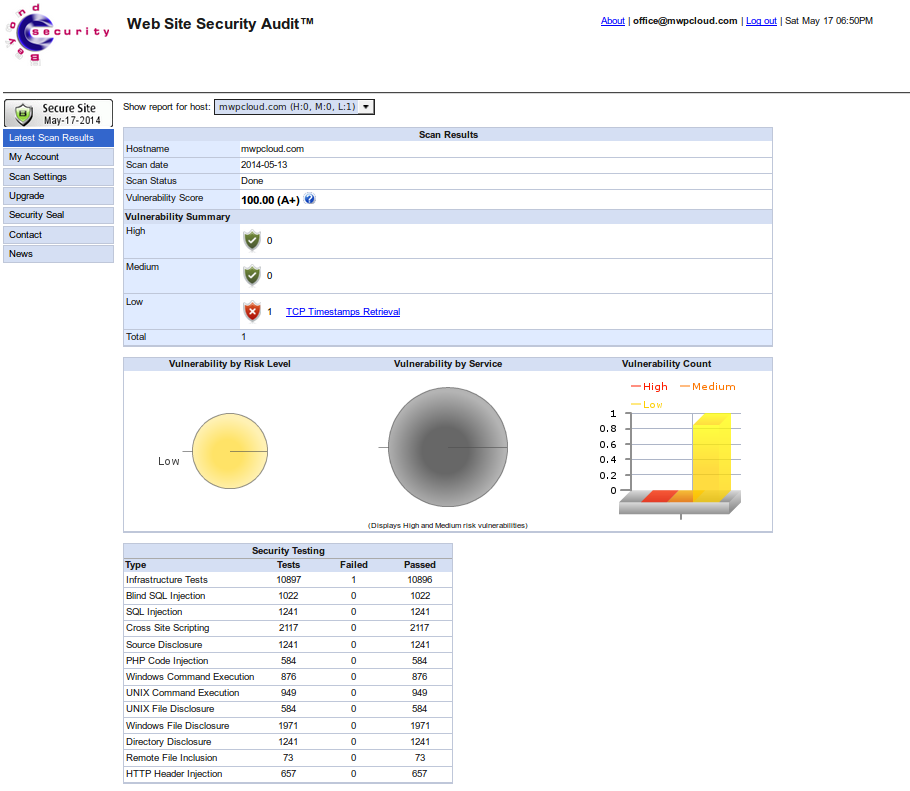
As you already know, CooliceHost.com hosts mWPCloud.com, an year old project, which we have launched in the upper class hosting services. While I was checking my email, I've found an email from the Security Audit of the mWPCloud scanner - Beyond Security - right now mWPCloud is located at the CooliceHost.com ssd server in Netherland. In other words, scanning the infrastructure of CooliceHost.com with the mWPCloud.com site. The same configuration with some changes we use on our hybrid VPS plans. Today someone has locked himself, so I decided to host him.
Here are the results:
1. First, I will tell you that there is no such thing as 100% security. It could be a bug somewhere into the scripts, or just an attack that we can not answer at the time, but only for now.
2. The result is one error in low, but it is not actually error, just following the RFC standard. Everything else is blocked successfully.
We will keep giving the best of us in order to achieve such a results!
And please, do not be sad at us, if the system logs you. One fake positive result could have 100 real treads.
Want to repeat it again - There is no such thing as 100% security.
Here are the results:
1. First, I will tell you that there is no such thing as 100% security. It could be a bug somewhere into the scripts, or just an attack that we can not answer at the time, but only for now.
2. The result is one error in low, but it is not actually error, just following the RFC standard. Everything else is blocked successfully.
1. TCP Timestamps Retrieval (Low)
Port: general/tcp
Summary: The remote host implements TCP timestamps, as defined by RFC1323. A side effect of this feature is that the uptime of the remote host can be sometimes be computed.

We will keep giving the best of us in order to achieve such a results!
And please, do not be sad at us, if the system logs you. One fake positive result could have 100 real treads.
Want to repeat it again - There is no such thing as 100% security.
Последно редактирано от модератор:
the.rampage.rado
Well-Known Member
Just want to give my special thanks to coolice, who helped me with the my first SSL installation. He has pointed me where I can get it cheaper than usual and also with the full installation. Works great even without buying another IP address. Everything is just perfect.
Последно редактирано от модератор:
coolice
Owner
Nginx, SSD hosting с cPanel and Varnish Cache - CooliceHost.com
There was a little update to PHP 5.429 and ioncube loader 4.6.1
Little Opnecart sites, that do not need a huge amount of traffic took advantage of the SSD speed, that we provide. They are as fast as light, according to the owners opinions, comparing to other hosting providers.
There was a little update to PHP 5.429 and ioncube loader 4.6.1
Little Opnecart sites, that do not need a huge amount of traffic took advantage of the SSD speed, that we provide. They are as fast as light, according to the owners opinions, comparing to other hosting providers.
Последно редактирано от модератор:
Rock
Well-Known Member
От: Ultra fast Nginx, SSD hosting with cPanel and Varnish Cache in Netherland
More feedback:
2 weeks since my transfer to coolice. My website is mainly visited by Bulgarians, so I've checked in WMT location Bulgaria. Also I've changed the cms and the site URLs are brand new. For 14 days all of my webpages were indexed (8K pages) and my google rankings are the same, even I got some natural traffic increase (due to the new cms I suppose). So do not worry about geolocation, the host won't hurt your rankings, at least mine was fine.
More feedback:
2 weeks since my transfer to coolice. My website is mainly visited by Bulgarians, so I've checked in WMT location Bulgaria. Also I've changed the cms and the site URLs are brand new. For 14 days all of my webpages were indexed (8K pages) and my google rankings are the same, even I got some natural traffic increase (due to the new cms I suppose). So do not worry about geolocation, the host won't hurt your rankings, at least mine was fine.
Blinky
Owner
Wow, thanks for your create feedback.  As more people saying the best hosting is the one that you never get to the support team.
As more people saying the best hosting is the one that you never get to the support team. 
Google solved this problem with the geolocation with their GWT, which tells them better, where to put your site. Many years ago we counted on IPs, C-classes, and so on. Now, all you need to do is writing on your mother language and pointing Google what to take as a location and that's it. Know sites, hosted in UK, that rank better in US, because they want to.
Google solved this problem with the geolocation with their GWT, which tells them better, where to put your site. Many years ago we counted on IPs, C-classes, and so on. Now, all you need to do is writing on your mother language and pointing Google what to take as a location and that's it. Know sites, hosted in UK, that rank better in US, because they want to.
uni-web
Well-Known Member
От: Търся програмист
Щом казваш, иначе чисто си ти трябва дизайнер, коденето на html, и css не се брои за програмиране, а за дизайн. И интересно, но сега за първи път чувам, че за промени по дизайн на сайт трябвали двама човека, тогава аз като реша да променям нещо по някой от сайтовете ми ще да си търся бригада от 5-6. Много правилно ти го е казал колегата, не се засягай, ама и да ми кажеш, че си щял да ме учиш през теб, не да ме обиди, ами ме облива в пълен смях.
Дано си намериш някой вчерашен пиклеш тук да ти се върже на написаното, ама надали. Със здраве.
Щом казваш, иначе чисто си ти трябва дизайнер, коденето на html, и css не се брои за програмиране, а за дизайн. И интересно, но сега за първи път чувам, че за промени по дизайн на сайт трябвали двама човека, тогава аз като реша да променям нещо по някой от сайтовете ми ще да си търся бригада от 5-6. Много правилно ти го е казал колегата, не се засягай, ама и да ми кажеш, че си щял да ме учиш през теб, не да ме обиди, ами ме облива в пълен смях.
Дано си намериш някой вчерашен пиклеш тук да ти се върже на написаното, ама надали. Със здраве.
Колега писал съм трябва ми програмист! Промените по дизайна на един сайт се правят от 2 човека. програмист и дизайнер. Без спам ако обичате ...
nnikolov
Active Member
От: Търся програмист
Колега... Не ми се занимава с глупости Има много видове дизайнери и не всеки дизайнер е задължен да знае html и css, както и да е. Незнам какво имаш предив под това "някой да ми се върже"? Аз не съм работил с доста хора от форума и всички са доволни от коректността ми. Не съм поредния ти далавераджия че да ми пишеш простутии.
Има много видове дизайнери и не всеки дизайнер е задължен да знае html и css, както и да е. Незнам какво имаш предив под това "някой да ми се върже"? Аз не съм работил с доста хора от форума и всички са доволни от коректността ми. Не съм поредния ти далавераджия че да ми пишеш простутии.
Жив и здрав!
Колега... Не ми се занимава с глупости
Жив и здрав!
uni-web
Well-Known Member
От: Търся програмист
Имам предвид, че казваш, че ще се учел някой програмист покрай теб, а реално искаш програмист за дизайн. Това, че някой ще напише един два дива със стила им не го прави програмист. Иначе не ми обръщай внимание тъкмо се разсънвам, със здраве, но просто като пишете трябва ми програмист за дизайн, че и двама човека трябвало за промяна по дизайна на сайт ми идва малко в повечко, за туй. И ти със здраве.
Имам предвид, че казваш, че ще се учел някой програмист покрай теб, а реално искаш програмист за дизайн. Това, че някой ще напише един два дива със стила им не го прави програмист. Иначе не ми обръщай внимание тъкмо се разсънвам, със здраве, но просто като пишете трябва ми програмист за дизайн, че и двама човека трябвало за промяна по дизайна на сайт ми идва малко в повечко, за туй. И ти със здраве.
Колега... Не ми се занимава с глупостиИма много видове дизайнери и не всеки дизайнер е задължен да знае html и css, както и да е. Незнам какво имаш предив под това "някой да ми се върже"? Аз не съм работил с доста хора от форума и всички са доволни от коректността ми. Не съм поредния ти далавераджия че да ми пишеш простутии.
Жив и здрав!
